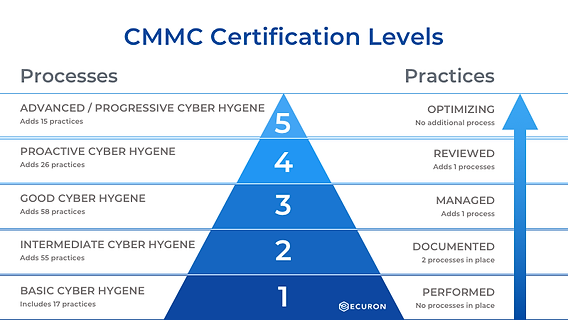
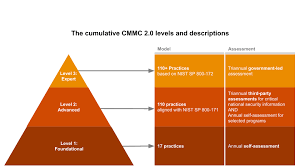
Deciphering Complex Requirements in the CMMC Framework, Let’s face it—decoding the Cybersecurity Maturity Model Certification (CMMC) can feel like trying to read a map with missing pieces. It’s packed with technical details, layered requirements, and nuanced standards. But what if we told you that understanding its intricacies doesn’t have to be overwhelming? With the right approach and tools like the CMMC Assessment Guide, even the most complex elements can become manageable steps toward robust cybersecurity compliance.
Breaking down technical jargon in the CMMC Assessment Guide into actionable steps
Deciphering Complex Requirements in the CMMC Framework, One of the most challenging aspects of CMMC is its heavy use of technical jargon. Terms like “access control mechanisms” or “incident response protocols” can feel more intimidating than they need to be. The CMMC Assessment Guide can turn these abstract phrases into concrete, actionable steps.
For example, instead of simply saying you need to “restrict access,” the guide might explain how to implement role-based permissions in your systems. It goes further by breaking this down into smaller tasks, like identifying which roles require specific levels of access and configuring those permissions accordingly. By treating jargon as puzzle pieces and focusing on practical implementation, you can demystify even the most complicated requirements.
The guide isn’t just a glossary; it’s a translator, bridging the gap between technical terms and actionable plans. This approach makes it easier to move from theory to practice, ensuring every step you take is meaningful and aligned with CMMC standards. Deciphering Complex Requirements in the CMMC Framework.
Prioritizing high-impact controls within the CMMC framework
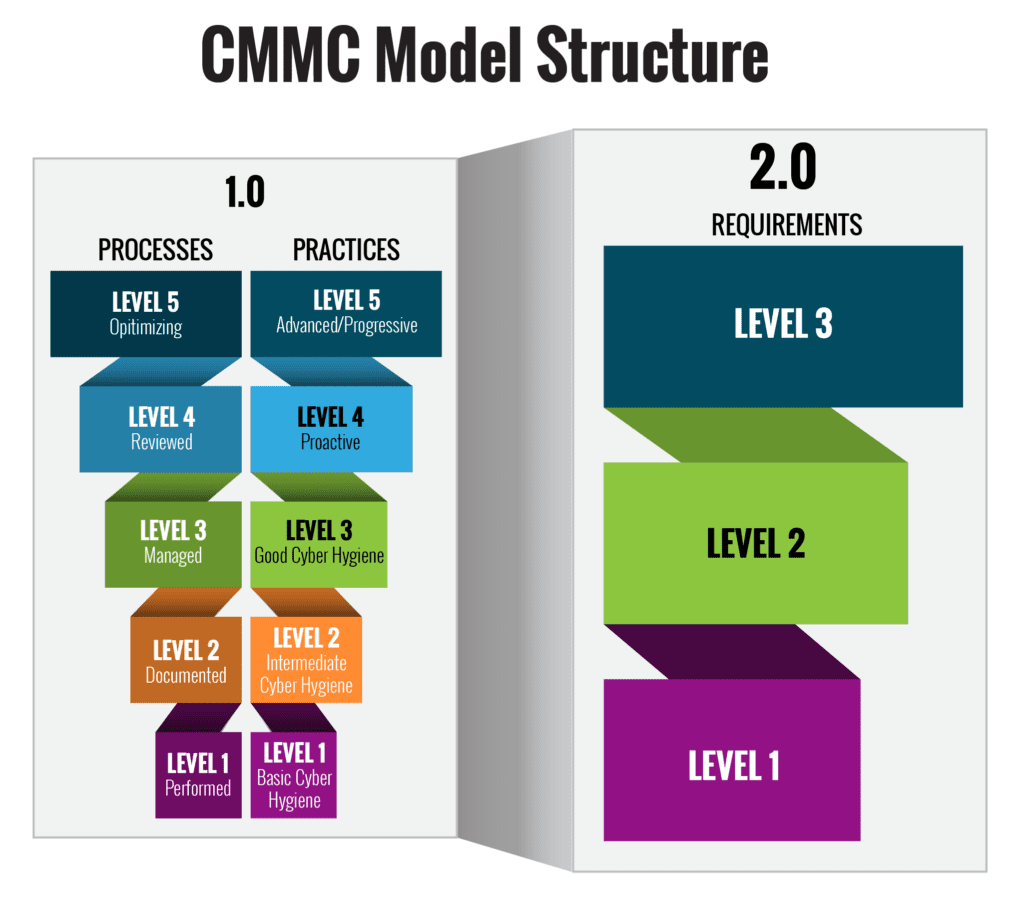
Start by identifying controls that protect the most sensitive data in your organization. These might include multi-factor authentication, encryption, or continuous monitoring systems. The CMMC Assessment Guide can help you pinpoint these critical areas, offering insights into which controls should take precedence.
Focusing on high-impact areas first allows you to build a strong foundation of security while working toward full compliance. It’s a smarter, more strategic way to approach the CMMC framework, ensuring you address what matters most without getting bogged down by less urgent details. Deciphering Complex Requirements in the CMMC Framework.
Using visual aids and flowcharts to simplify the CMMC process
Deciphering Complex Requirements in the CMMC Framework, Let’s admit it—long lists of requirements and pages of documentation can feel overwhelming. Visual aids like flowcharts, graphs, and diagrams can bring clarity to the CMMC process, helping you see how different pieces fit together.
For instance, a flowchart could outline the steps to establish a security operations center, showing how initial assessments, technology implementation, and ongoing monitoring connect. These visuals can make abstract processes tangible, helping everyone in your organization understand their roles. Deciphering Complex Requirements in the CMMC Framework.
The CMMC Assessment Guide often inspires such creative approaches by organizing information into structured sections. Taking it a step further and translating that structure into visual formats can save time, enhance comprehension, and improve collaboration across teams.
Collaborating across teams to interpret multi-faceted CMMC standards
Deciphering Complex Requirements in the CMMC Framework, CMMC compliance isn’t a solo endeavor. Achieving certification requires input from multiple departments, including IT, human resources, and leadership. Collaborative efforts ensure that every facet of the framework is interpreted correctly and implemented cohesively.
Start by creating cross-functional teams tasked with tackling specific areas of the CMMC requirements. For example, IT can handle technical controls, while HR oversees employee training programs. Regular check-ins ensure that everyone stays on the same page, avoiding gaps or overlaps.
The CMMC Assessment Guide can act as a shared resource during these collaborations. By referencing the guide together, teams can align their efforts, clarify ambiguous requirements, and streamline the compliance process. This cooperative approach not only simplifies CMMC but also strengthens organizational communication and culture.
Leveraging expert insights to clarify nuanced CMMC requirements
Deciphering Complex Requirements in the CMMC Framework, Even with the best intentions, some CMMC requirements can still feel unclear. This is where expert insights come in. Professionals familiar with the framework can shed light on nuanced areas, ensuring you don’t misinterpret or overlook critical details.
The CMMC Assessment Guide often serves as a starting point for these discussions, providing a solid foundation of knowledge. Experts can then help you navigate complex scenarios, such as tailoring controls to meet both CMMC standards and your unique business needs.
Don’t hesitate to ask questions or seek clarification. Expertise paired with a comprehensive guide can bridge the gap between uncertainty and confidence, making the entire process smoother and more effective.
Testing compliance measures to ensure alignment with the CMMC Assessment Guide
Deciphering Complex Requirements in the CMMC Framework, The final step in deciphering the CMMC framework is testing your compliance measures. It’s not enough to implement controls—you need to verify they work as intended. Regular testing ensures your efforts align with the CMMC Assessment Guide and its standards.
This might involve running penetration tests, simulating security incidents, or conducting internal audits. These activities reveal weaknesses, highlight areas for improvement, and build confidence that your systems are audit-ready.
Testing isn’t just about passing certification—it’s about maintaining a resilient cybersecurity posture. By regularly assessing your measures against the guide, you create a continuous improvement loop that keeps your organization secure and compliant over the long term.